"Thousands of Humana customers have their medical data leaked online by threat actors"
https://securityaffairs.co/wordpress/120402/data-breach/humana-data-leak.html
The leak comes more than four months after Humana, the third-largest health insurance company in the US, notified 65,000 of its health plan members about a security breach where “a subcontractor’s employee disclosed medical records to unauthorized individuals” between October 12, 2020, and December 16, 2020. In May, one of the patients affected by the breach filed a lawsuit against the company.
Related new: https://www.hipaajournal.com/humana-and-cotiviti-facing-class-action-lawsuit-over-63000-record-data-breach/
On May 26, 2021, a lawsuit was filed in the U.S. District Court for the Western District of Kentucky over the mishandling of Humana insurance plan members’ medical records. Humana had contracted with Cotiviti to handle medical records requests to send to the HHS’ Centers for Medicare and Medicaid Services (CMS). Cotiviti had subcontracted some of the work to Visionary Medical Systems Inc.
About Visionary Medical Systems Inc : https://www.bloomberg.com/profile/company/4067733Z:US
Visionary Medical Systems Inc. develops medical software solutions. The Company designs and develops practice management software for medical billing, electronic health record, and management modules to provide point-of-care, for flow sheet snapshots capturing critical patient information, chronic disease tracking, alerts, and reporting mechanisms.
"CompuGroup Medical to acquire 100% stake in Visionary Healthware Group" : https://www.tmcnet.com/usubmit/2010/09/01/4986799.htm
Sep 01, 2010 (Datamonitor Financial Deals Tracker via COMTEX) -- CompuGroup Medical AG, a Germany-based provider of software and communications solutions, has entered into an agreement to acquire 100% stakes in American Healthcare Holdings, Inc. (AHH), Visionary Medical Systems, Inc. (VMS) and Visionary RCM, Inc. (VRCM) (collectively, Visionary Healthware Group).
This will get interesting
Takeaways
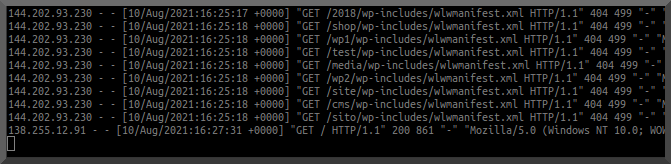
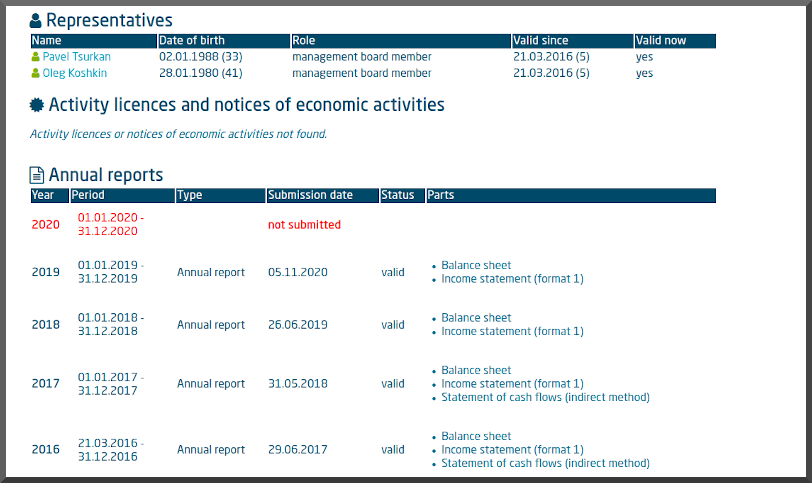
1. 6,487 individual health records are for sale. The record owners will not be paid.
2. This new wealth of PII will make identity theft easy for somebody
3. If you leak the wrong person's information they will sue you.
4. I think CompuGroup is being targeted by an APT group. (see MedNetwoRX ransomware attack.)
Questions
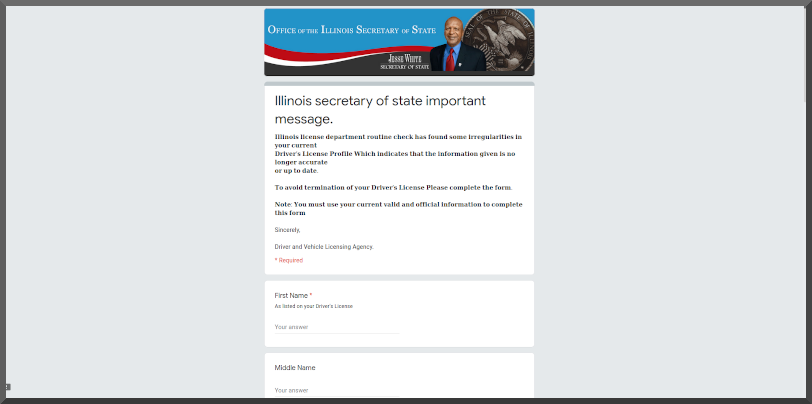
1. What "personal coding business endeavor" was the employee responsibile for the breach attempting to create
2. Why does everybody get "complimentary membership to Equifax’s credit monitoring and identity theft protection services for two years". Equifax was no better.
3. Was it technically a CompuGroup breach?
-A. Buford
July 22nd, 2021


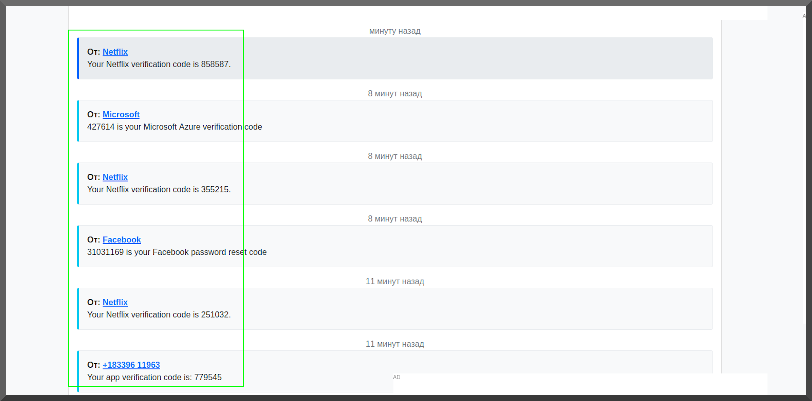
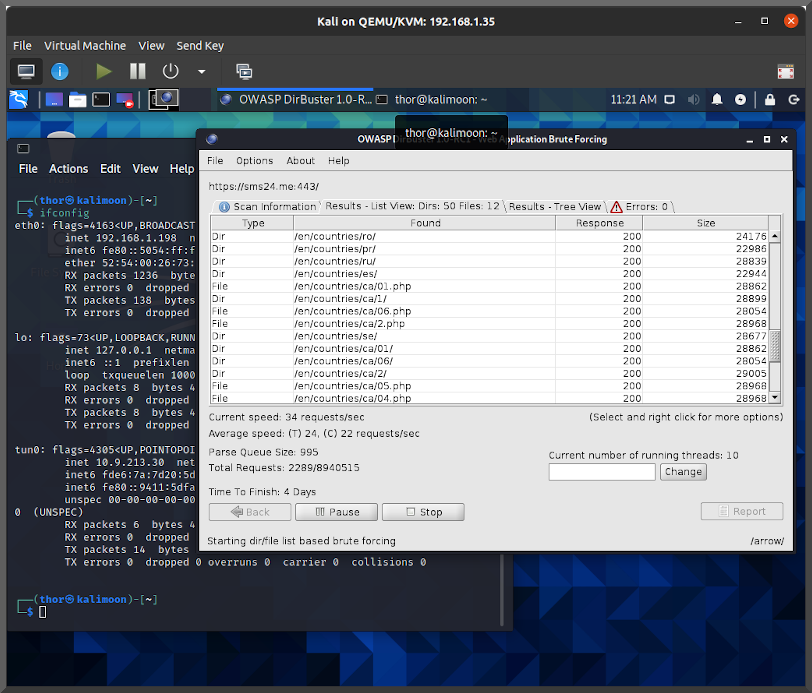

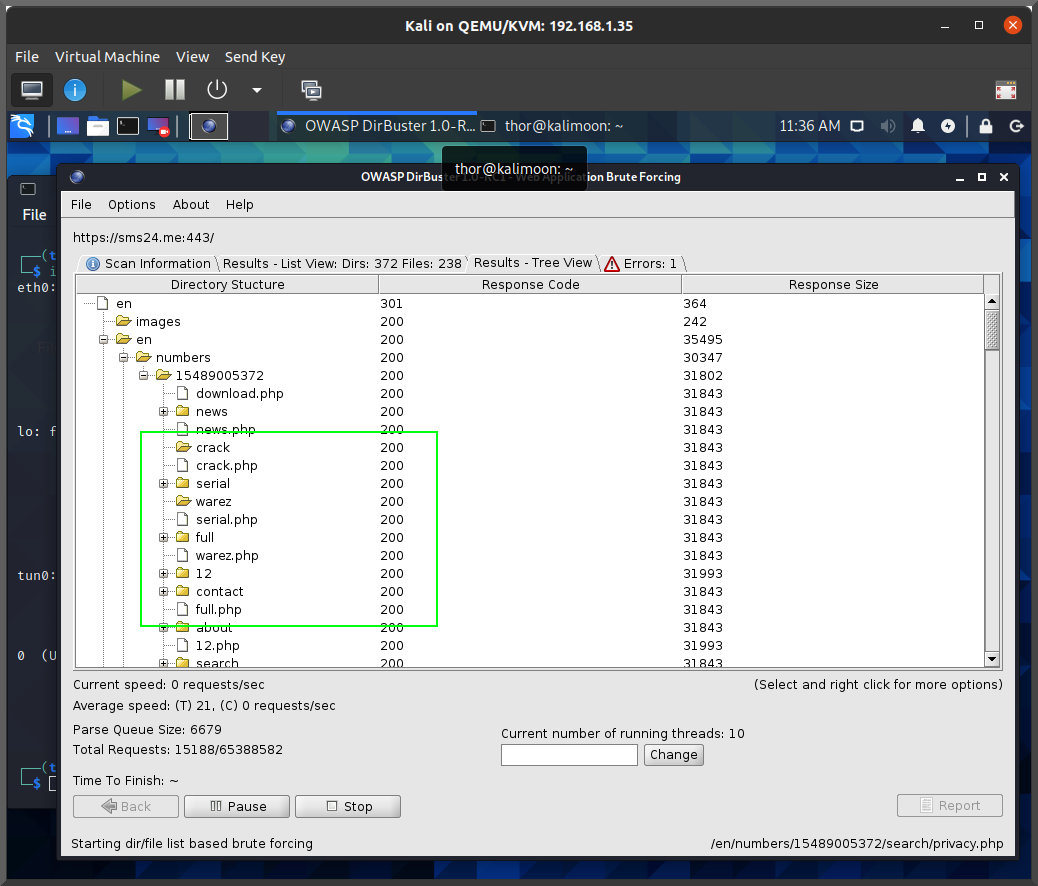
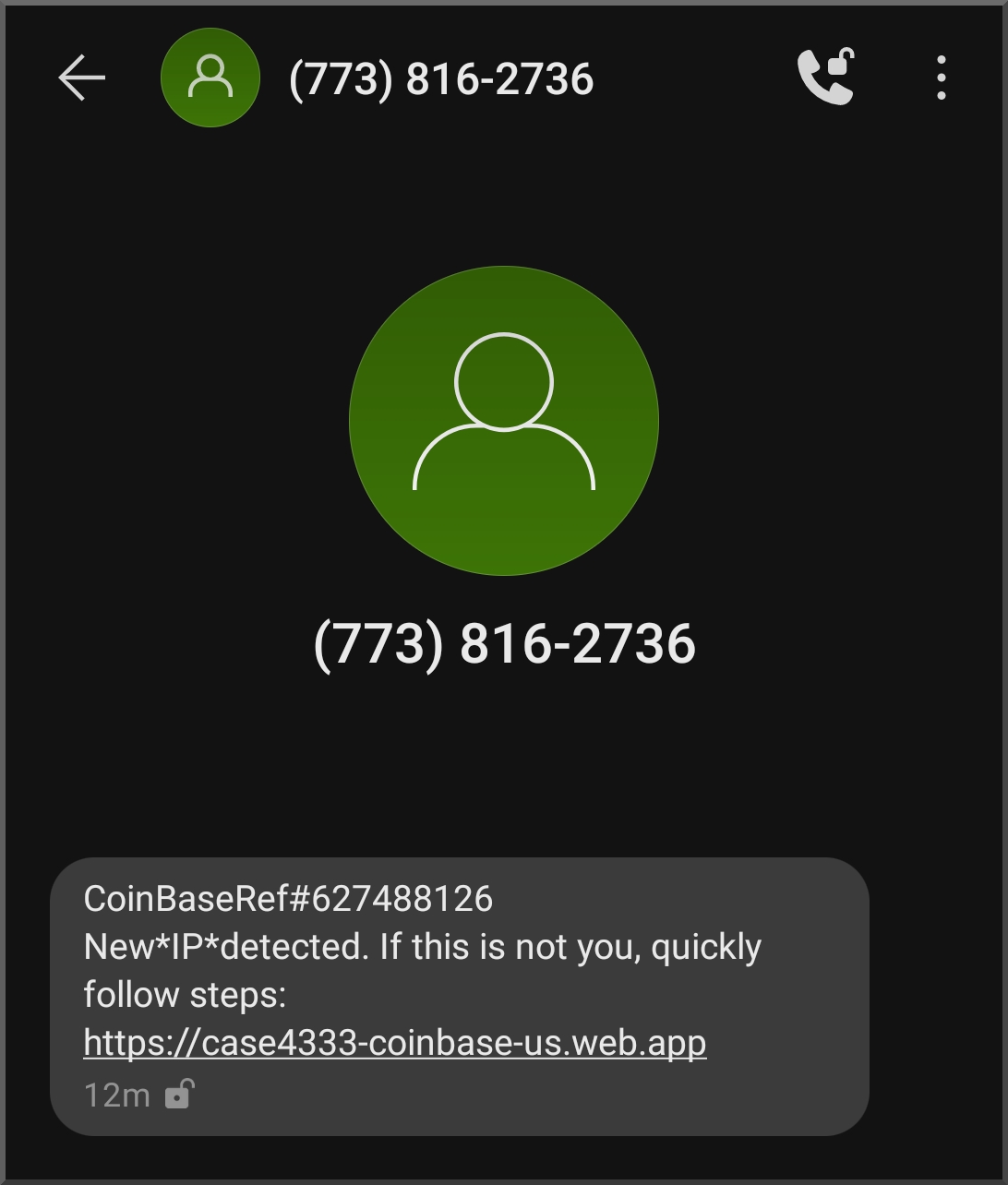

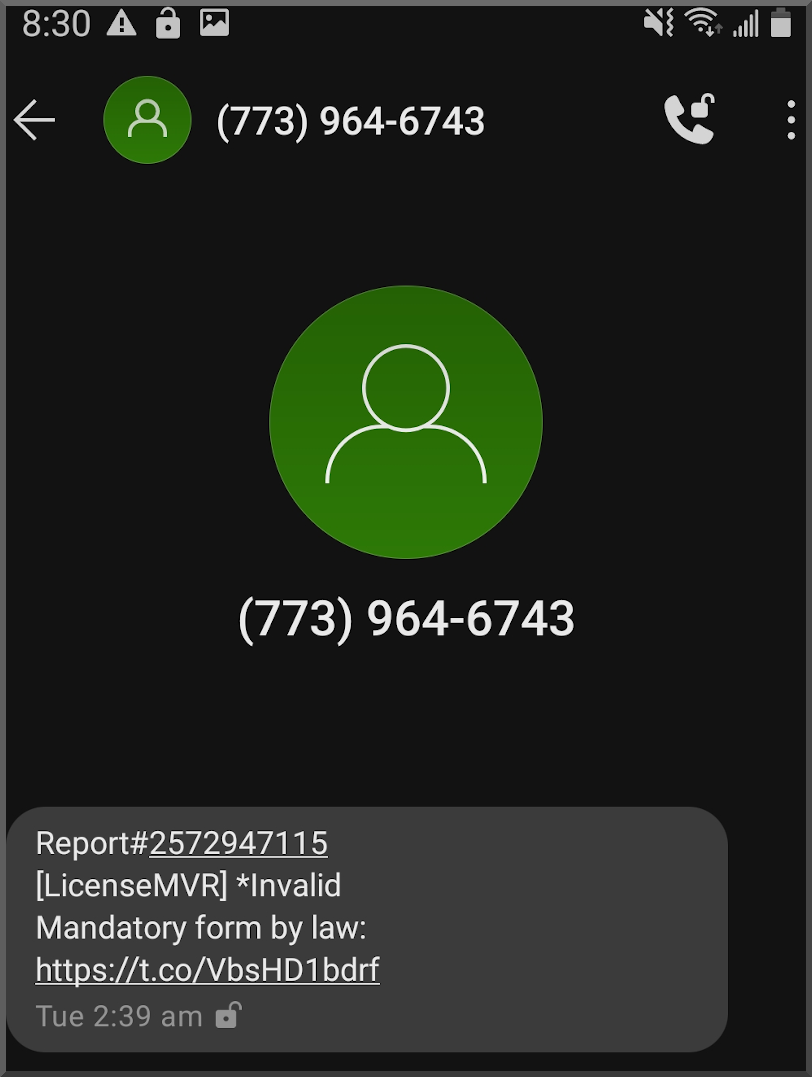
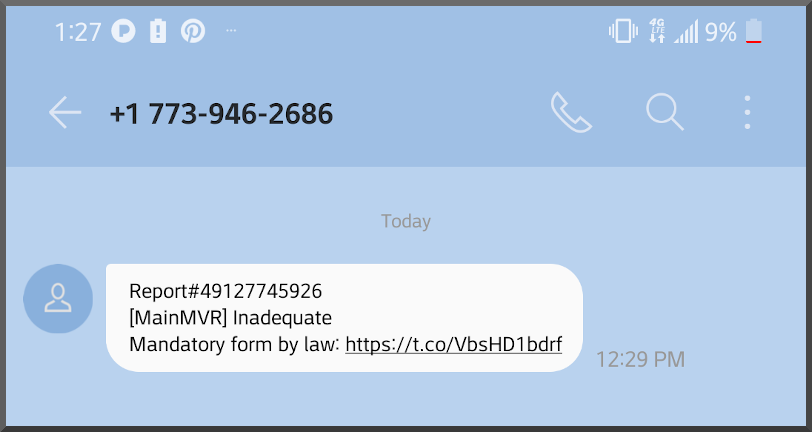
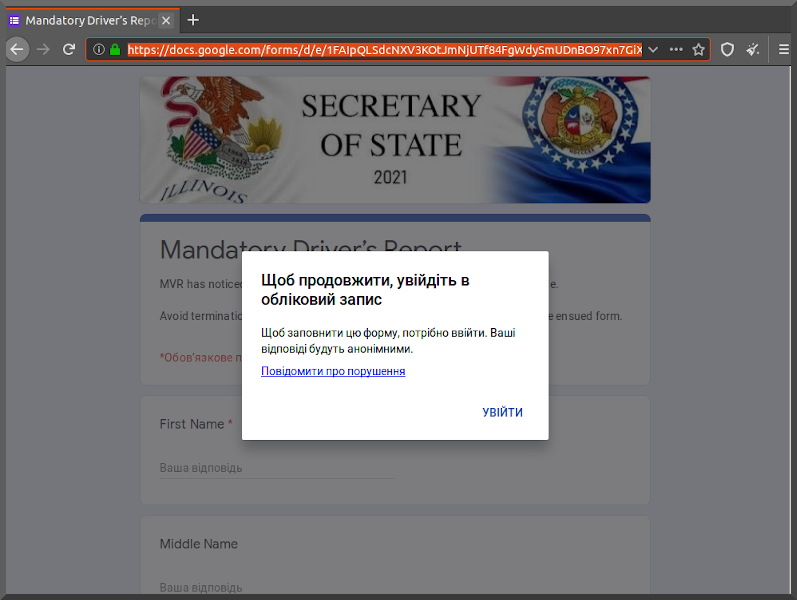
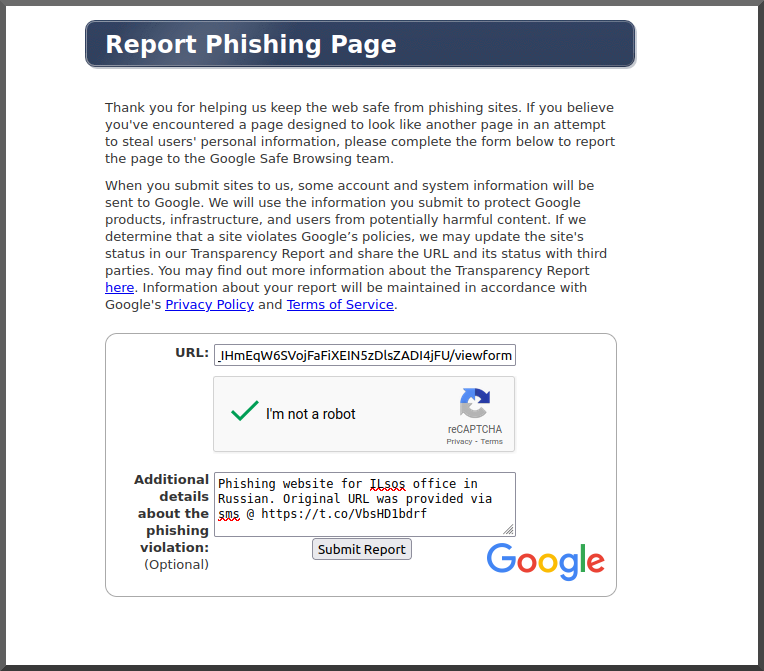

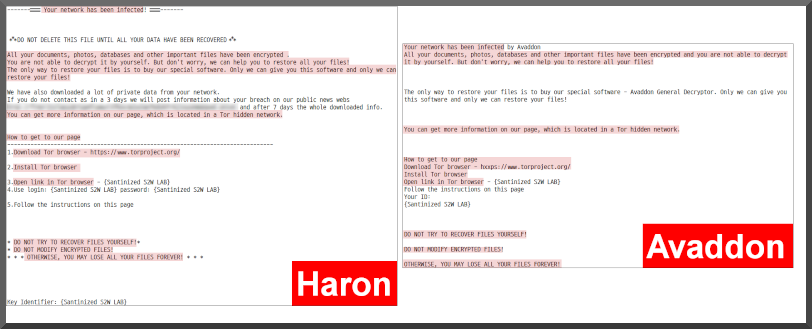
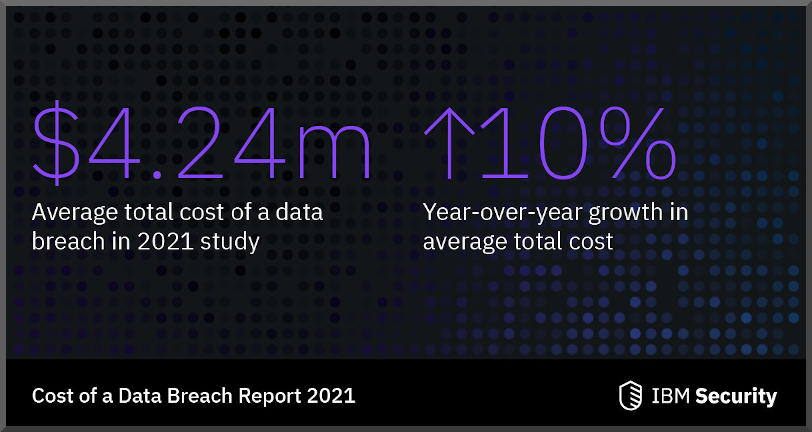







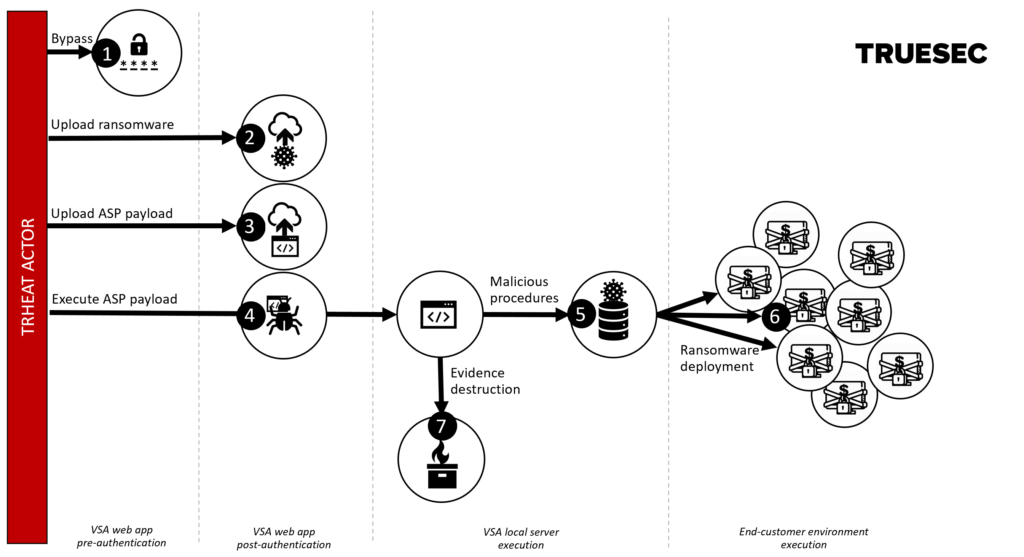



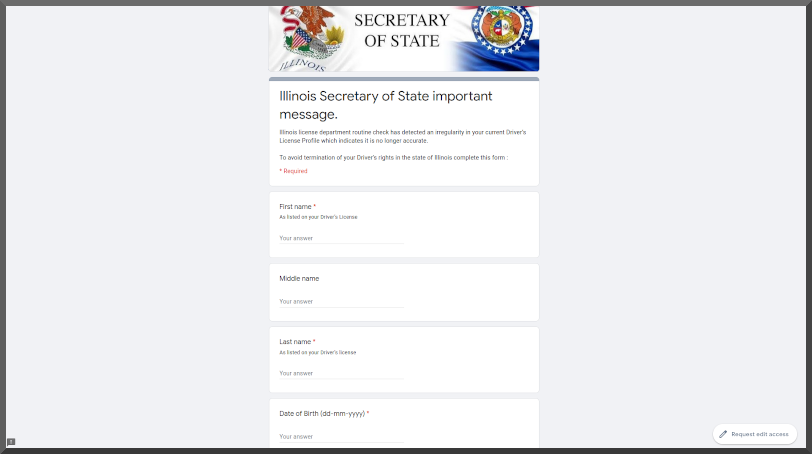
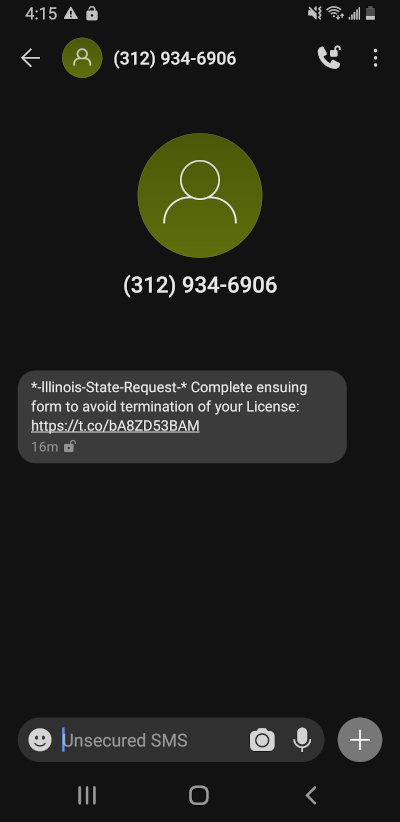
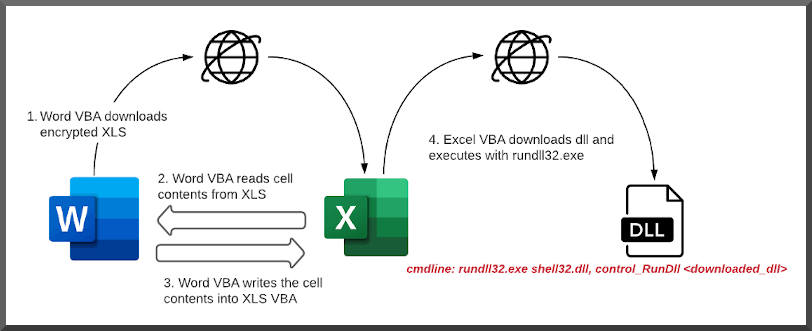
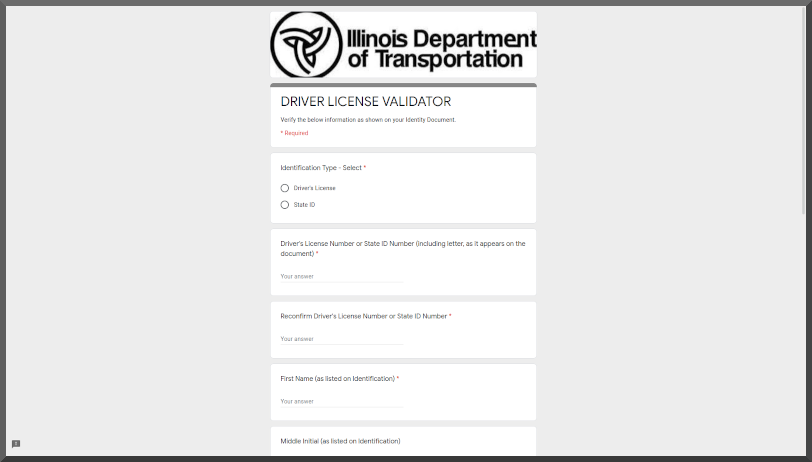
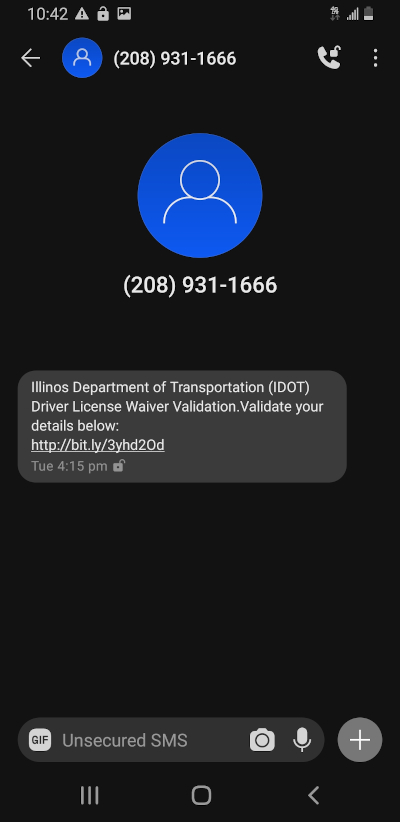


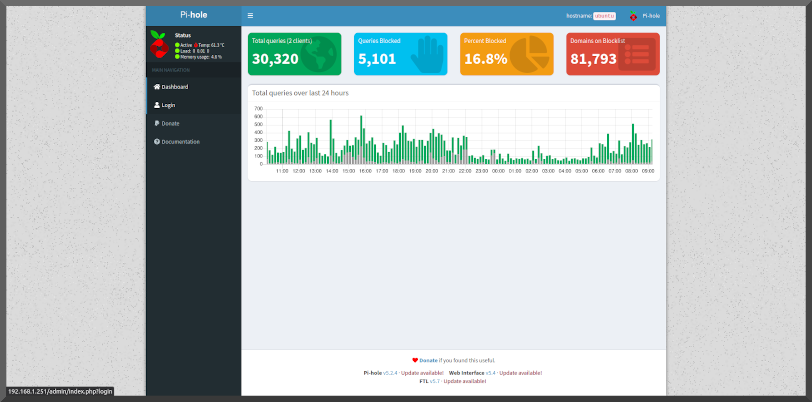



 Too tired to code anything more interesting to say "yay I finished"
Too tired to code anything more interesting to say "yay I finished"
 I just reached Chapter 10 of the Sybex book. It reads pretty quick and easy with some Kid Cudi in the background. It's like heaven on earth. Hopefully I am able to finish the text in next day or so. I really want to focus on the video material... and then see what other free materials are available online. I've invested approximately $80 so far in this certification process. The test itself is another $300(ish).
I just reached Chapter 10 of the Sybex book. It reads pretty quick and easy with some Kid Cudi in the background. It's like heaven on earth. Hopefully I am able to finish the text in next day or so. I really want to focus on the video material... and then see what other free materials are available online. I've invested approximately $80 so far in this certification process. The test itself is another $300(ish).