They were POSTing all along. Rookie mistake.
A family-friend-client tasked me with the purpose of figuring out why their, self-hosted, web server was receiving so much traffic but their product statistics, customer feeback, and lack of business leads did not reflect an uptick in traffic.
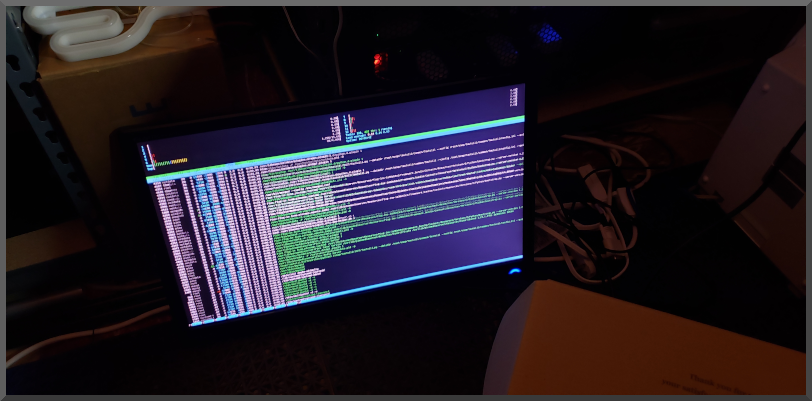
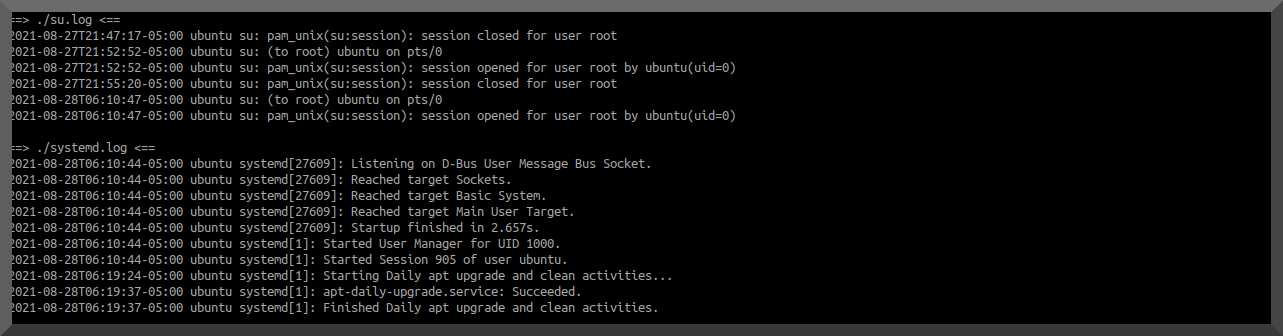
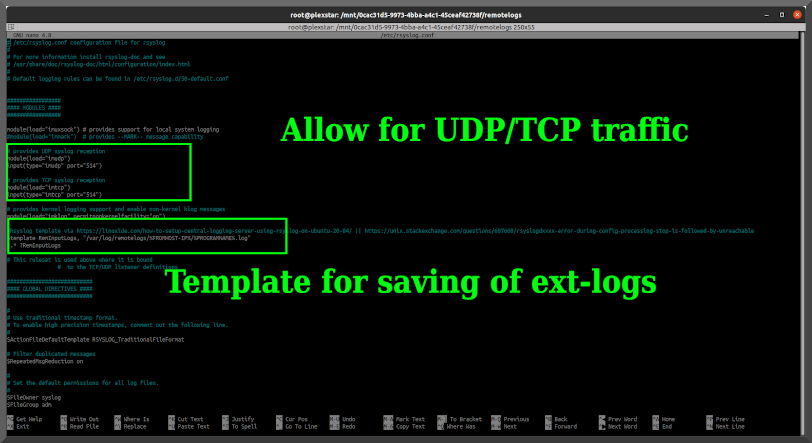
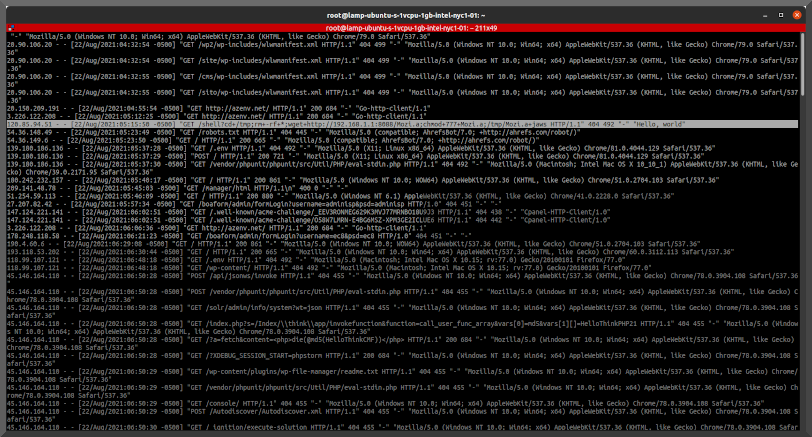
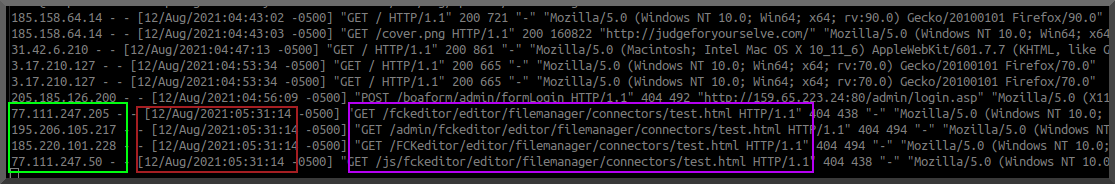
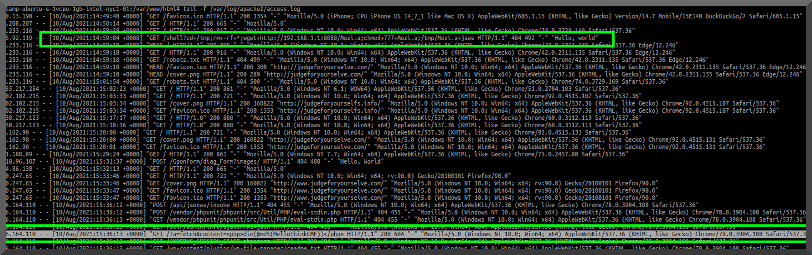
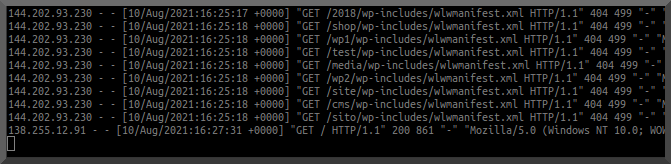
IF more people are visiting than normal then sales SHOULD be up right? Typically. Unless it is being used for something 'else'. Next step: view the logs!.
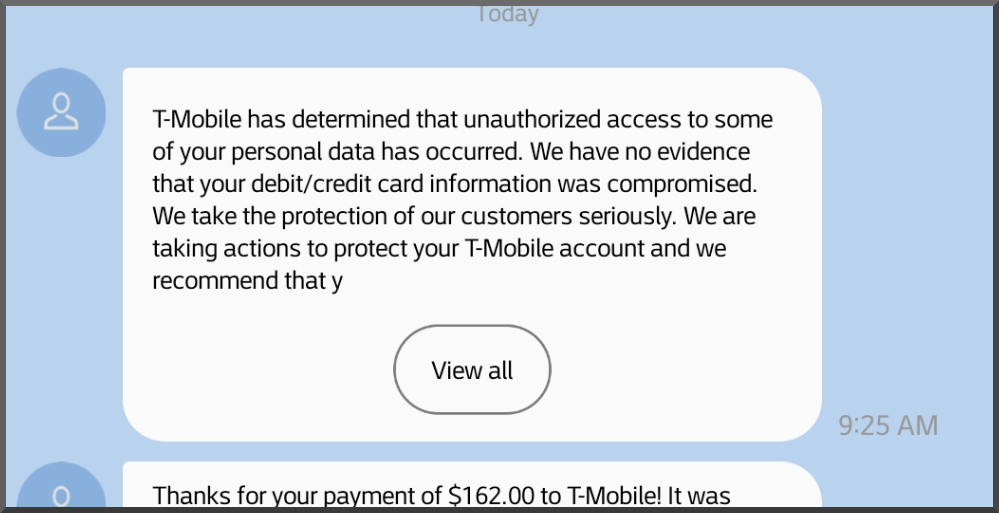
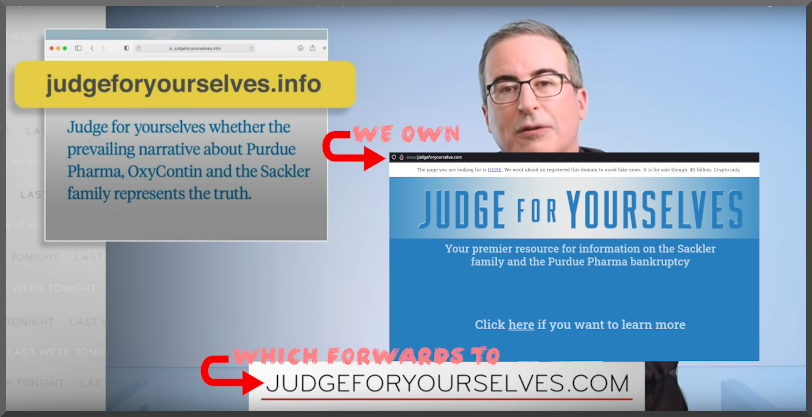
As I assumed the server was being used as a relay for posting of screen captures. Malicous or not.. the traffic isn't related nor wanted. Guess what ip address shows up in the log for the POST request FROM his server? Yeah, no bueno!
Apache is not very secure by default. It needs to be hardened. I simply enabled the rewrite module and appended some Rewrite Rules to the htaccess file. Bam!
sudo a2enmod rewrite Enable module
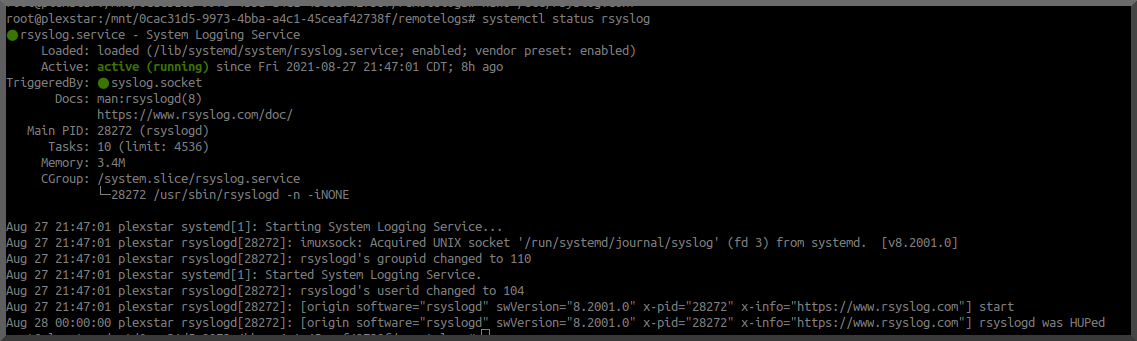
sudo systemctl restart apache2 Restart Apache to load Rewrite module
RewriteCond %{REQUEST_METHOD} POST
RewriteRule .* - [F,L]
In addition to the above I did advise 'Mike' that the logs would have to be monitored and rewrite rules modified, semi-continuously, to remove ALL unwanted traffic. "Businesses do not have IT departments only for when poo hits the fan. They are also there so the smell doesn't even reach the office."
A. Buford
Oct, 18th 2021

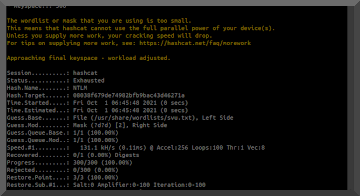
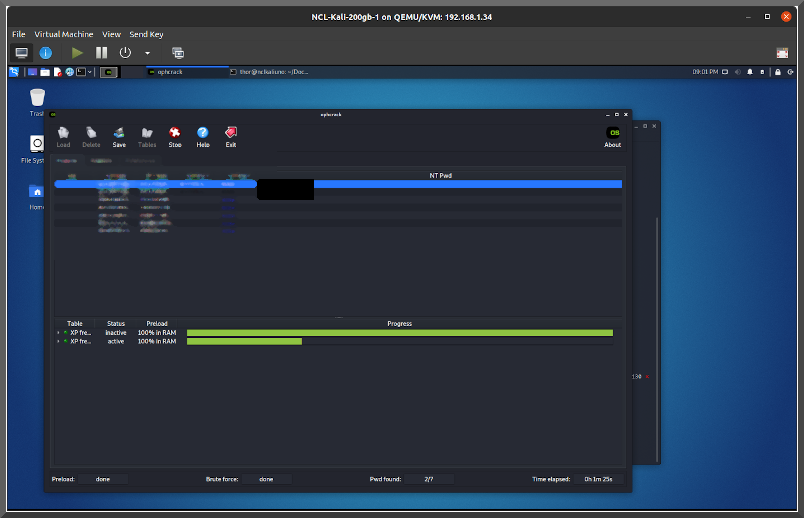



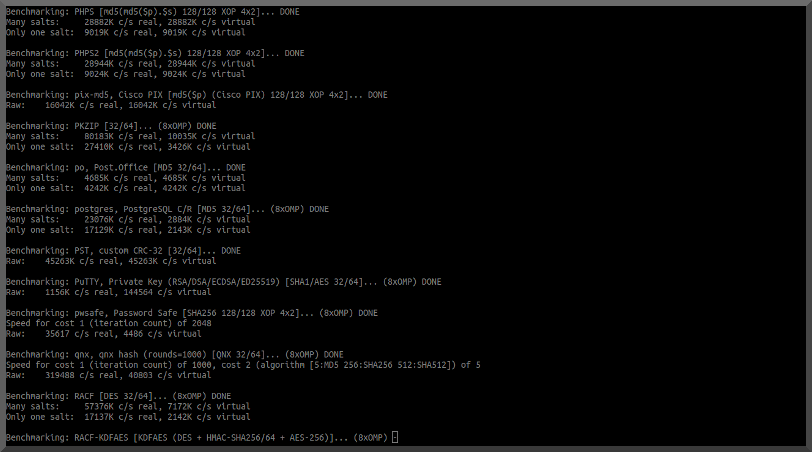
 ..and I didn't. So it appears you still have to build yourself for gpu support. I'll revisit after Samba configuration is perfected.
..and I didn't. So it appears you still have to build yourself for gpu support. I'll revisit after Samba configuration is perfected.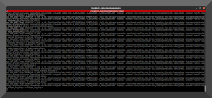 More info @ https://kalitut.com/john-the-ripper/
More info @ https://kalitut.com/john-the-ripper/